Why We Built Secure.com: From a 99% Market Gap to Force Multiplier
Traditional security left 99% of businesses behind with fragmented tools, overworked teams, and manual defenses.
Traditional security left 99% of businesses behind with fragmented tools, overworked teams, and manual defenses.

Traditional security left 99% of businesses behind — fragmented tools, overworked teams, and manual defenses that can’t keep up with AI-powered attackers. Secure.com was built to fix that. With a unified data foundation, adaptive AI-teammates, and automated remediation for routine threats under human oversight, it delivers the speed, context, and scalability needed to defend at machine pace — finally making enterprise-grade protection practical for SMBs and mid-market teams.
After two decades of building and protecting digital platforms, one truth became unavoidable: cybersecurity was never built for the majority. The world’s largest organizations command the best tools and budgets, while the rest — fast-moving mid-market and SMB teams — face the same threats with a fraction of the resources.
The result? A widening 99% Market Gap — the space between those with limitless security budgets and those defending everything with duct-taped stacks. Secure.com was built to close that gap.
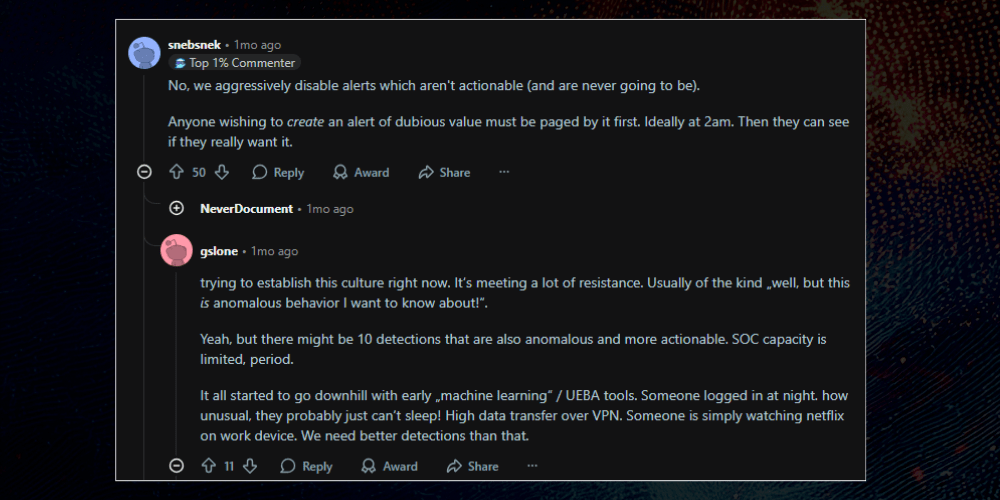
This is not a vendor story. It’s the story of practitioners who lived the same pain: alert fatigue, tool sprawl, and broken automation that promised relief but delivered chaos. It’s also about what happens when you rebuild security for speed, scale, and sanity — with AI as the operating paradigm, not an afterthought.
Attackers move at machine speed; defenders still move at human pace. Across the industry, analysts wrestle with too many tools, too much noise, and too little time.
Two structural forces define the crisis:
That’s where the founder's realization began: the problem wasn’t a lack of tools — it was architectural. Fragmentation has become the biggest threat surface of all.
For two decades, security innovation chased complexity — not accessibility. Most solutions were engineered for enterprise SOCs with sprawling budgets. For everyone else, that model collapses under its own weight.
Secure.com started with a simple premise: If 99% of businesses face the same attackers as the top 1%, their defense stack must deliver the same capability — minus the complexity.
Legacy architectures created what we call security’s architectural debt — decades of patchwork tools held together by brittle scripts.
The breakthrough came when we stopped optimizing legacy workflows and started redesigning the foundation itself.
(Source: Reddit)
The platform was built from a clean slate, to unify, automate, and adapt. Three design principles define that vision:
Security starts with visibility. Secure.com consolidates telemetry from endpoints, identity, network, and cloud into a single indexed layer, enabling AI to reason with full context.
Instead of brittle scripts, Secure.com uses AI-teammates that autonomously triage, investigate, and act, escalating only what requires human judgment. Analysts move from “doer” to “validator,” gaining leverage without losing control.
Routine containment is automated; critical actions require human sign-off. Continuous evidence collection replaces painful audit cycles with ongoing assurance, merging compliance into operations.
Secure.com was created to address several persistent challenges:
Secure.com was designed to protect the vast majority of organizations that are underserved by traditional SOC, SIEM, and SOAR solutions. While conventional tools leave gaps in visibility and operational coverage, Secure.com provides AI-first security, automated remediation, and real-time asset intelligence to ensure teams can respond effectively across cloud and SaaS environments.
Unlike conventional platforms that rely heavily on manual processes and human intervention, Secure.com integrates AI into every aspect of its operations. It automates threat detection, incident investigation, and risk assessment while providing real-time asset intelligence. This AI-first methodology allows organizations to respond to threats faster, reduce alert fatigue, and maintain continuous protection without the operational bottlenecks typical of legacy tools.
Secure.com unifies visibility across cloud, SaaS, and hybrid environments, automatically discovering assets and tracking changes. By combining continuous monitoring, automated classification, and AI-driven insights, it ensures that SOC teams can detect threats early, protect AI assets, and maintain end-to-end security coverage.
What began as an internal necessity evolved into a platform others needed too, a blueprint for defending at machine speed without losing the human element.
(Source: Reddit)
Organizations that rely solely on traditional security platforms face increasing risks as AI-driven threats emerge. Without AI-first security, SOC teams struggle with blind spots, slow response times, and unmonitored AI workloads. This leaves them exposed to shadow AI, prompt injection attacks, and data misuse, while alert fatigue and tool sprawl further limit their ability to maintain digital trust and cloud security across SaaS and hybrid environments.
Secure.com continuously monitors AI pipelines and SaaS environments using advanced AI SecOps capabilities. It identifies anomalies, detects prompt injection attempts, and flags shadow AI activity. Automated workflows and remediation allow SOC teams to respond in real time, reducing reliance on manual processes while maintaining continuous monitoring and visibility across all assets.
Traditional SOC, SIEM, and SOAR tools were designed for conventional IT assets and static workloads. They cannot detect threats unique to AI, such as adversarial attacks, model theft, or prompt injection. AI pipelines require continuous asset intelligence, real-time monitoring, and automated remediation—capabilities that legacy platforms lack. Without AI-first security, organizations risk exposure and delayed threat response.
Shadow AI refers to unauthorized or unmonitored AI systems running within an organization. Secure.com discovers and classifies these hidden assets using AI-driven asset intelligence, continuously monitoring them for risk. Automated alerting and remediation ensure shadow AI is either secured or brought under governance, helping maintain compliance, digital trust, and operational resilience.
Secure.com stands out through its combination of AI-first security, digital teammate support, and end-to-end automation. Key differentiators include:
Secure.com wasn’t built as a product pitch — it was built as a survival response to a broken system. After years of watching security teams drown in noise and complexity, we realized the industry didn’t need another dashboard. It needed digital teammates — systems that unify, adapt, and give people their leverage back.
The 99% deserve the same caliber of defense as the top 1%. By combining unified data, adaptive AI, and autonomous operations, Secure.com makes that possible.
The old way was built for machines pretending to be human. The new way is built for humans operating at machine speed.

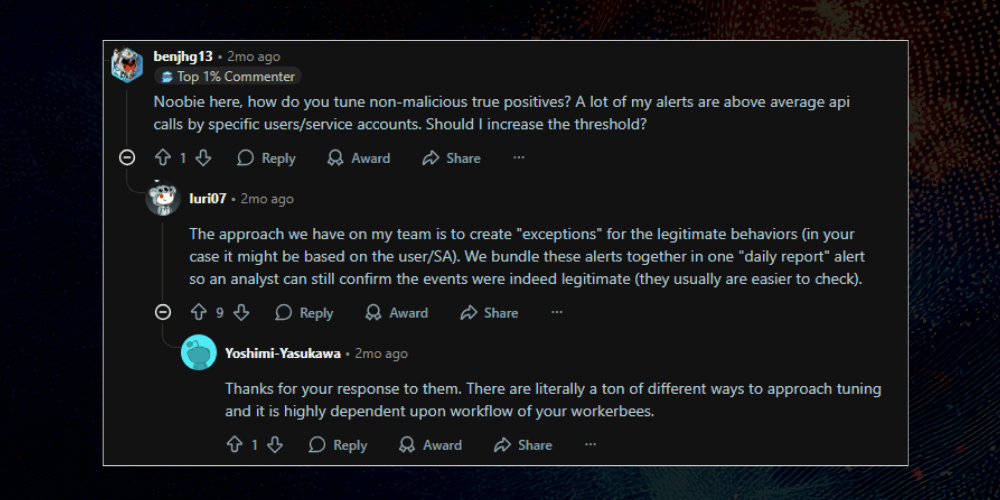
Alert fatigue drains SOCs by burying them under endless, low-value alerts and false positives, leading to burnout and missed threats.

The Security Leverage Gap widens when tools add visibility but not velocity; closing it requires Digital Security Teammates that amplify human capacity through governed autonomy.