Alert Fatigue is a Choice: A Smarter Path to Incident Triage and Response
Alert fatigue drains SOCs by burying them under endless, low-value alerts and false positives, leading to burnout and missed threats.
Alert fatigue drains SOCs by burying them under endless, low-value alerts and false positives, leading to burnout and missed threats.

Alert fatigue drains SOC teams by burying them under endless, irelevant alerts and false positives, leading to burnout and missed threats. The fix isn’t adding tools—it’s rethinking triage. Smart automation, intelligent filtering, and contextual correlation can cut through the noise, reduce false positives, and refocus analysts on real risks.
Alert fatigue is draining security teams. Analysts face a flood of warnings, thousands a day. Many of them are false positives. Others don’t matter. Yet every alert demands time, and there aren’t enough hours in the day.
Studies show that up to 70% of alerts are noise, which means teams spend more time filtering than fighting real threats. The result? Burnout. Missed attacks. Slower response.
It’s no longer a workload issue. It’s a business risk.
This blog explores what causes alert fatigue, why it persists, and how to fix it, without wearing your team down in the process.
Alert fatigue happens when security teams are bombarded with so many alerts that they start to ignore, overlook, or dismiss them. It’s not a sign of laziness. It’s the brain’s natural response to overload.
Most SOCs run multiple tools, and each one sends alerts for possible threats - malware, failed logins, suspicious traffic, misconfigurations. On their own, these alerts might be helpful. But together, they create a big volume of undifferentiated alerts and hide what truly matters.
Analysts try to keep up. They triage tickets. They chase down logs. They escalate what looks dangerous. But over time, something happens: their focus slips. High-priority threats start to look like all the rest. Mistakes happen. Breaches get missed.
Alert fatigue isn’t just a team issue. It’s a system issue. And it starts with too many signals, not enough context.
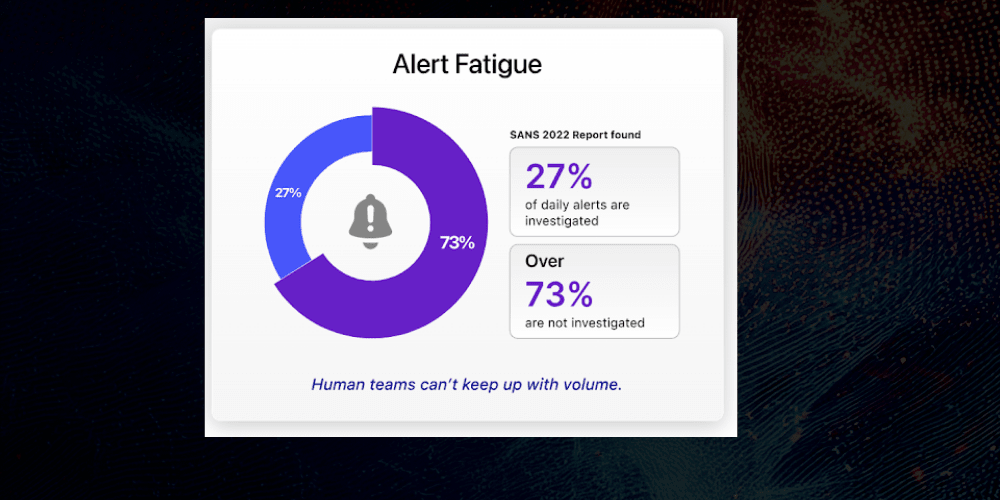
Alert fatigue stems from one core problem: security alert overload. Modern SOCs are overwhelmed not because they lack tools, but because they have too many. Each system—SIEM, EDRs, firewalls, CSPMs—fires off alerts in isolation, most of which lack contextual relevance and proper risk prioritization.
The result?
Multiple security tools often generate redundant or noisy alerts, especially SIEMs. Instead of clarity, they create alert storms with little correlation or context.
Many SOCs report that over 50% of daily alerts are false alarms. This not only wastes analyst time and increases MTTR but also erodes confidence in the system.
Without smart filtering, everything appears urgent. Critical threats get buried under low-value noise, making effective threat response nearly impossible.
Alert fatigue doesn’t just slow teams down-it wears them out. Constant noise, endless triage, and false urgency drain focus and morale. Over time, it leads to cybersecurity burnout, especially in lean teams already under pressure.
The average security analyst workload includes hundreds of alerts daily, based on tool configuration and threat type. But they’re not just managing alerts, they’re switching between tools, chasing logs, escalating cases, and documenting everything. The human-in-loop cost adds up.
When teams are overwhelmed, operational fatigue sets in. Analysts miss key signals. Response times stretch. False negatives rise. The organization's risk posture weakens not because of a lack of talent, but because of fragmented tools and insufficient process automation framework.
Worst of all, real threats don't slow down. Attackers exploit distraction. They slip through the noise while teams chase what looks urgent, not what matters.
In SecOps and cybersec teams, fatigue is a liability. And if your team is drowning in alerts, it’s not a workload problem - it’s a workflow problem.
There’s a better way to handle alerts, and it doesn't involve hiring dozens of analysts or turning off noisy tools. The key is shifting from manual triage to automated alert triage.
Smart triage means using rules, behavior models, and AI to decide what matters and what doesn’t . To prioritize alerts intelligently before human reviews. Instead of reacting to everything, your system filters noise, surfaces real threats, and connects the dots automatically.
This is where incident response automation steps in. By automating the first 60–70% of investigation tasks-enrichment, correlation, and even containment - security teams use SOAR to free up time for real decision-making.
The best solutions use AI in incident response not to replace analysts, but to supercharge them. They pull context from your asset inventory, user behavior, threat intelligence, and logs for more accurate decision-making.
It's not just faster; it's smarter. And it moves teams out of firefighting mode and into a more strategic, threat-driven rhythm.
Reactive alert management manages alerts as individual fires that needs to be extinguished. This reactive model creates constant firefighting, where teams are just waiting for the next alert, wasting 80% of their time on triage instead of prevention.
Whereas, Proactive alert management changes this model via predictive intelligence, contextual automation, and behavioral baselines to anticipate incoming threats before escalation.
You don’t need to rebuild your entire security program to fix alert fatigue. You just need to start smart by reducing noise, reclaiming time, and building automation into your workflows.
Your first step will be to identify the real source of the noise. SIEMs, EDRs, and cloud tools have the potential to overwhelm teams with alarms (if they're not properly tuned). For whatever tool is generating alerts, track where these alerts come from, how many you receive, and how many of the alerts you have are false positives. Before long, you'll recognize which tools are generating noise, but not value.
Don't treat every alert like a separate fire. Use alert correlation tools to connect the dots across systems. One high-risk event backed by three low-fidelity signals is still one incident, not four different tickets. Smart correlation cuts noise and reveals patterns humans miss.
Start by automating repetitive and high-volume tasks like tagging, alert enrichment, and initial classification, which can free up complex investigations. When alerts are enriched with context and scored before reaching a human, your team saves time and sanity.
Many teams treat symptoms instead of the source. But if your thresholds are too low or your alerts too sensitive, you're creating the problem. Fine-tune alert logic, suppression rules, and escalation paths. Small tweaks lead to a sharp drop in security alert overload.
Burnout isn’t just caused by alerts, it’s caused by the belief that nothing can change. Involve your team in tuning workflows. Let them flag what's broken. When they see that alerts are smarter, not just fewer, they engage again. That's how you reduce security analyst workload for good.
The short answer is yes. The long answer is that intelligent filtering can minimize false positives by 50% within the first quarter of implementation. SOC teams need to move beyond threshold adjustments to behavioral filtering and context-awareness that figures out what’s normal for your environment. Some modern fileting techniques that lean SOC teams can use are as follows:
Most security teams don’t suffer from a lack of alerts; they suffer from too many. If you’re wondering how I should restructure my incident response process to minimize alert fatigue, Secure.com helps lean security teams with AI-driven tools to reduce noise and enhance the highest risk alerts, allowing them to focus resources where they matter.
Instead of adding more tools to manage alert noise, Secure.com uses built-in automation and AI to handle triage. Alerts are enriched with context, scored by risk, and automatically grouped when related. This reduces manual sorting and improves visibility into real threats.
The platform applies automated alert triage and threat prioritization to filter out low-risk or repetitive alerts, especially those tied to known false positives or routine activity. This cuts down on distractions and helps teams respond faster.
Secure.com connects signals from SIEM, cloud, endpoint, and identity tools into a single dashboard. Analysts no longer need to switch between platforms to understand what’s happening. This central view helps with faster investigation and resolution.
By reducing alert volume and automating first-level investigation steps, Secure.com helps prevent cybersecurity burnout. Teams spend less time on repetitive triage and more time on higher-impact response and threat hunting.
Secure.com gives teams the power to make quicker decisions through smart alert correlation tools and contextual workflows, with no risk of missing real threats. The outcome is faster response times and less operational fatigue.
<faq><fq>What metrics should I track to measure alert fatigue in my SOC?</fq> <fa>Check MTTA (Mean Time to Acknowledge), alert-to-incident ratio, alerts closed without investigation, and false positive rates. Track human factors such as job satisfaction surveys, absenteeism, and analyst turnover. </fa></faq>
<faq><fq>What are the most common causes of alert fatigue in modern security operations? </fq> <fa>The most common causes are poorly-configured detected rules, tool sprawl creating similar alerts, and no contextual information, forcing SOCs to investigate events manually. </fa></faq>
<faq><fq>What role does alert tuning play in preventing alert fatigue? </fq> <fa>Alert tuning optimizes early detection rules by streamlining normal behavior, refining correlation logic, and adding exception lists for activities. Lean SOC teams can minimize volume by 50% while enhancing detection quality by allowing security analysts to focus on only high-fidelity signals. </fa></faq>
<faq><fq>Can I use machine learning to reduce alert fatigue in my security operations? </fq> <fa>Yes, you can use machine learning, but try to implement it very carefully. Machine learning can help you triage by learning from analyst decisions, grouping related alerts, and minimizing false positives. To become successful, you need security expertise, constant maintenance, and training data. </fa></faq>
<faq><fq>How do I know if my team is suffering from alert fatigue? </fq> <fa>Look out for increasing response times, emerging backlogs, real incidents being missed, and alerts closed without investigation. You have systematic alert fatigue that needs immediate intervention if your lean SOC team can’t take a few days off work without the queue collapsing on their heads. </fa></faq>
Alert fatigue isn’t inevitable; it's a symptom of outdated processes, noisy tools, and reactive security operations. Modern threats demand a smarter approach, one that leans on intelligent triage, automation, and risk-based prioritization.
By shifting away from manual, alert-by-alert response models and toward contextual automation, security teams can cut through the noise, reduce burnout, and stay ahead of what really matters.
In an era where every second counts, reducing alert fatigue isn’t just about improving workflows-it’s about improving outcomes.

Traditional security left 99% of businesses behind with fragmented tools, overworked teams, and manual defenses.

The Security Leverage Gap widens when tools add visibility but not velocity; closing it requires Digital Security Teammates that amplify human capacity through governed autonomy.